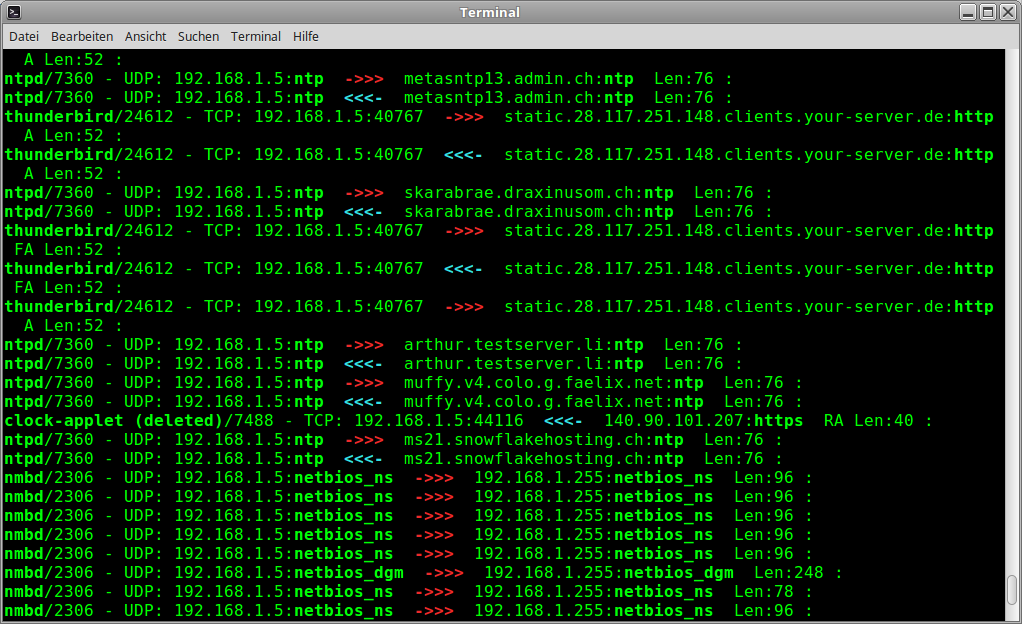
Network sniffer with application link
|
|
3 недель назад | |
|---|---|---|
| 400px-Terminal_059.png | 8 лет назад | |
| Changelog | 3 недель назад | |
| README.md | 3 недель назад | |
| Terminal_059.png | 8 лет назад | |
| sisniff | 4 недель назад |
README.md
sisniff
Sisniff is a network sniffer like tcpdump, that outputs all packets on a network interface from and to the local computer.
As a special feature, the corresponding application that sends or receives each packet is displayed.
Filter options can be used to track a specific application.
It supports TCP, UDP and ICMP packets, both on IPv4 and IPv6
All IP-level BPF-filters that can be used by tcpdump are also supported.
For HTTP connections, there are arguments (-H resp. -Hl) to display short or long payloads.
For DOMAIN connections, there is an argument (-D) to display DNS payload.
Under some cirumstances the program/PID cannot be evaluated. This mavericks would be reported as follow:
"?/?" = No entry in /proc/net/[TCP/UDP/ICMP] "-/-" = Found Inode but no PID "./." = The Inode found is '0'
!! sisniff uses scapy's sniff() function, so scapy package is needed:
!! debian: apt-get install scapy
!! pip: pip/pip3 install scapy
!! other systems: http://www.secdev.org/projects/scapy
This program needs Python 3.x or Python 2.x.
Homepage (german): https://wiki.zweiernet.ch/wiki/sisniff
Direct Download: wget https://git.zweiernet.ch/sigi/sisniff/raw/master/sisniff
Recent Version is 1.7.0
--------------------
# sisniff -h
usage: sisniff [-h] -i {eth0,lo,wlan0} [-n] [-P] [-p program|not-program] [-4] [-6] [-H] [-Hl] [-D] ["filter"]
sisniff V1.7
2017-2026 by sigi
positional arguments:
filter Filter (BPF syntax) on top of IP (in dbl-quotes "...")
optional arguments:
-h, --help show this help message and exit
-i {eth0,lo,wlan0} Interface
-n Do not resolve IP-Addresses
-P Don't put interface into promiscuous mode
-p program|not-program
Filter by program name (accepts * for matching) ([not-] negates)
-4 Only IPv4
-6 Only IPv6
-H Show HTTP Payload
-Hl Show HTTP Payload, long output
-D Show DNS Payload
--------------------
- Interfaces showed in the help are gathered from the running system.
programis meant the base name of the program/application, e.g.-p thunderbird-binprogramcan contain '*' pattern at the beginning and/or the end, e.g.-p thunder*not-programexcludes the program from beeing showed, e.g.not-thunderbird-bin. The '*' pattern also is accepted.filteris BPF-filter syntax as used by tcpdump. Must be written in double-quotes "..."
Example Commands
# sisniff "port not ssh" # sisniff -p *vpn* # sisniff -i wlan0 -p not-thunderbird-bin -4 "host not www.zweiernet.ch" # sisniff -i eth0 -p firefox -Hl "port 80"
Example Output